Enhance your business with outsourced IT support
IT support has changed. Break-fix solutions no longer apply. As your IT environment grows and becomes more complex, the concept of depending on IT support only when needed is no longer sufficient. Instead, as your business reliance on IT expands, a managed service approach monitored by a team of IT professionals can discover and solve problems before your productivity is compromised.
Read More...Watch Out for Phishing Attacks Hidden in Your Email
Online criminals know we are all busy, and that we often aren’t focused on what we are opening, reading and where we are clicking. They take advantage of that inattention by forging email messages to look like they've come from Apple, Facebook, and Amazon, along with well-known banks, payment services, retailers, and even government agencies such as the IRS and the Social Security Administration. Even more dangerous are messages that appear to come from a trusted individual and include personal details—often targeted at executives and company managers.
Generally speaking, these attacks are called phishing. And they cost businesses hundreds of millions of dollars every year.
The goal, of course, is to prompt you to click a link in the message and visit a malicious website. That site usually continues to masquerade as being run by a company or organization you trust. Its aim is to sucker you into revealing confidential information by asking you to log in, pay for a product or service, or fill out a survey. The site — or an attachment in the email message — might also try to install malware. Although macOS is quite secure, it can still be affected if you approve certain security prompts.
Here’s how you can help identify potential phishing attacks. Read More...
A backup triple play that ensures data safety.
Hope is not a strategy when it comes to protecting your valuable data. If you hope your data never becomes wiped, lost, hacked or manipulated, you’re already in trouble.
It is not optional to back up your Mac®. Backing up your computer on a regular basis protects your professional and personal data against loss, theft, damage or corruption. Backups offer the iron-clad insurance you need for fast recovery at work and at home.
But don’t assume that a single backup to an external hard drive or even a drive on your desk is good enough. It’s not. Because a fire or flood at your office or home may not be selective as to the damage it causes. Plus, if you rely on your Mac to get your work done, you may not want to wait as long as it will take to restore from certain types of backup devices.
Here is a triple-play backup strategy will help you avoid virtually all of these problems.
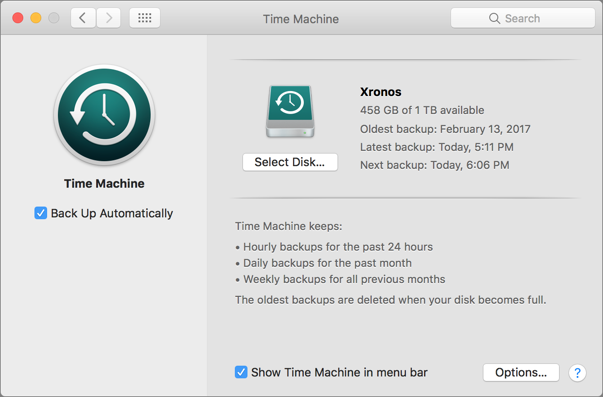
Backup #1: Time Machine
Apple® has been making backups easier since 2007 by providing Time Machine® software with the Mac. Set it up with an external drive and it will cheerfully create versioned backups that contain multiple copies of each file as it changes over time. With versioned backups, you can restore a lost or damaged file to its most recent state, or to any previous state. That’s essential if corruption crept in unnoticed and you’ve been backing up a corrupt file for some time. Time Machine also enables you to restore an entire drive as of the latest backup, which you might do if you have to reformat or replace your drive.
Keeping up? Create custom apps to automate tedious business processes
1Password Is the Solution for Password Protection
Every. Single. Site.
You’re doing that, right?
Most of us use our pet’s name with a birthdate stuck on the end or something similar. And we use the same password for multiple sites because 1) it’s too difficult to remember a different password for every site, 2) we don’t keep a record of every password we create, and 3) we’re just plain old lazy. Read More...
Make CrashPlan Your Backup Plan
You don’t have to be caught unaware if your computer crashes. Read More...
Endpoint Protector 4 Protects Your Company’s Greatest Assets
Endpoint Protector 4, a full Data Loss Prevention (DLP) and Mobile Device Management (MDM) product available for Windows, Mac OS X, Linux, iOS, and Android mobile devices, can help eliminate the risk by protecting your network and sensitive data from these types of threats. It will also help your company maintain compliance with HIPAA and other privacy regulations. The product provides protection in several different ways depending on the system or device. Read More...
Kerio Connect - Business Class Email
Kerio Connect Offers Features, Function and Reliability in an Affordable Mail Server
The days before email became essential to doing business seem like a theme for a documentary on the History Channel. Gone are the days when businesses relied solely on snail mail and phone calls to communicate. Email is a critical component to business success and the ability for your mail server to multitask is just as important. Ask yourself a few questions to determine if your email server is adequately meeting your current needs.
- Can you synchronize email messages between your phone and computer?
- Is the endless barrage of spam making it hard to find the real messages sent to you?
- Can you see and update the same list of contacts on your phone and your computer?
- Are you able to send and receive meeting invites that sync with your calendar?
- Can you easily set an out-of-office message and schedule it to turn on and off by itself?
Maximize Teamwork and Efficiency with Soonr
It’s not news that teamwork is essential to business success. You’re only as strong as your weakest link and all that jazz. To keep your team functioning at highest capacity, they need to be able to collaborate efficiently; however, workplace collaboration can be a real challenge for businesses with employees who work remotely or from different office locations. Even if all your staff works in the same building and on the same floor of that building, ensuring that each person is working with the most current version of any particular file or project can seem like a juggling act with updates flying fast and furious, usually via email . The result is multiple versions of the same project in various stages of update -- in other words, a big mess. This is where a file management and document sharing tool like Soonr can help.
Read More...Xero Accounting Software - Quickbooks Alternative
Inevitably, this conversation leads to them asking about what we use in our offices, because if it works for us, then surely it will work for them. While we can’t guarantee that perfect match 100% of the time, quite often it is true.
We think this applies to Xero accounting software. It’s what we use at CranstonIT and we have an expert available to set it up for you and train you how to use it.
Read More...
Pulling the Curtains on Your Electronic Window
Today is your lucky day! There are more people than you can possibly imagine who want to know everything about you and are willing to pay for this information. They’re just not willing to pay you. And you’ll never actually meet them, either.
Have you ever noticed that immediately after shopping online for area rugs, you start to see rug ads in the margins of the web pages you visit or in the ads that appear in your Facebook timeline? Spyware and trackers are used by many companies as a marketing tool. It’s a form of adware that tracks your internet browsing habits and uses this data to deliver in-page ads targeted specifically to you. Read More...
Be Ware of Ominous Pop Up Warnings in Your Browser
One popular way these internet scumbags attempt to lure us into their evil web is to plant an ominous warning that pops up on our monitor foretelling of grave danger ahead if we don’t act fast.
“Warning!” it says. “Your computer has a malicious virus.”
The message is almost always accompanied by a tech support phone number. Call this number and they are only too happy to bill your credit card a hefty sum. Read More...
Collaborate Like a Pro and Save Money
Promotion extended till September 30th, 2015
If you’ve been struggling to find a simple way for your staff, consultants, clients, vendors, and anyone else who makes up your team to collaborate on projects and easily communicate status updates, assignments, changes and revisions, Samepage is the way to go. This multi-use tool puts all of your project’s components in one place, lets you assign tasks, and makes it easy for your team’s players to communicate without the need for multiple file sharing, messaging, and project management programs.
Read More...
Drowning in spam? Here’s how to send those spammers running.
Spam, or unsolicited emails sent to a large number of recipients, is an unfortunate byproduct of our online activity. Anytime you share your email address, you increase your chances of receiving spam. This includes posts made to online forums or web sites, online order forms that require an email address, web site registrations, job inquiries, blog subscriptions, and even emails sent to friends. Some companies share your information with partner vendors, while others sell it to the highest bidder. Even if you only share your address with a select few, if your friend’s account is hacked, the spammers gain access to their address book.
It’s easy enough to stop legitimate spam received from companies you know. Simply click the unsubscribe link at the bottom of the email to be removed from the mailing list. This will either unsubscribe you immediately or take you to a preferences page where you can unsubscribe altogether or limit the number and frequency of emails you receive. Marking this type of message as “Junk” often doesn't work well because businesses try very hard to craft messages that ensure their emails do not end up in a Junk folder. Read More...
Protect Your Computer and Save Money with this Special Sale on a UPS
Fortunately, there is an easy way to protect yourself against these types of issues. Uninterruptible Power Supplies (UPS) are a surge protector and battery backup in one. When storms rage around you, you can keep working since your computer system is safe. At CranstonIT, we believe that UPS systems are an important part your computer network both at the office and home. A UPS system is a relatively simple piece of hardware and having the “newest” version really isn’t any different than having an “old” version except that you get to pay more. The important part of a UPS is its battery. You need a good quality battery that is less then three years old.
 Read More...
Read More...Slack: Redefining Business Team Communication
LibreOffice: A Free Alternative to Microsoft Office
Wouldn’t it be nice if there was a software solution, that ran great on Mac, could open, edit and create files that were seamlessly compatible with Microsoft Office and didn’t cost a small fortune? LibreOffice is a solution to the office suite dilemma that not only provides all these features, but it’s also free. You can create “Word” documents, “Excel” spreadsheets, “PowerPoint” presentations and more all without paying a dime! Read More...
SSL Poodle Bug
Custom Business Solutions
As a small business ourselves, we at Cranston IT understand that there are lots of challenges that the modern small business face. You may need to be able to access your important data from different locations such as your office, warehouse, production floor or on the road. It is often critical that your information stays up to date or you may need to create a workflow process that employees can follow. Maybe you’re looking to make the transition from working on paper to electronically or perhaps you are trying to eliminate double entries of data. Whatever problem your business is looking to overcome, we at Cranston IT have a solution. Read More...
Samepage - Online Collaboration for your Business
DuckDuckGo Search Engine Review
Recover Your Lost Data w/ Gillware
If that crash does occur and you realize you didn’t back up your data, then what? There are still recovery options available through professional data recovery services. These services can be expensive but if your critical data is on a failed drive, it can be well worth the price of recovery. Read More...
Expand your mind with iTunes U
1Password - Effective Password Management
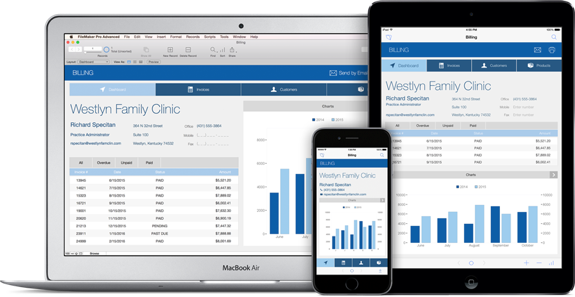
FileMaker 13 - A Step Forward in Business Management
FileMaker just released FileMaker 13. This new version introduces Web Direct. It’s now possible to get the full FileMaker experience through a web browser. That means that FileMaker can now be accessed directly from a web browser on your desktop or laptop. The FileMaker software no longer has to be installed on a computer. The connection is direct to the live database. Changes are immediately available just like you were working in the FileMaker Pro application. Read More...
Backup. Now. Before It's Too Late
Our professional data backup service safeguards your data up to the minute. It’s automatic and continuous, and we securely store your data on enterprise-grade servers at off-site data centers. Read More...
FileMaker Databases for your Business
We recommend FileMaker Pro. This database software has been an industry leader for small and medium size businesses for over 20 years. It’s cross platform and data can be accessed from your Mac, Windows PC, web browser or iOS Device. Multiple users can access the database simultaneously from anywhere there is an internet connection. Read More...
Integrate Google Maps into your FileMaker database
With the integration of ProMaps, the locations of your projects, contacts or any other needed address records are beautifully displayed so that you can keep track of all that is going on in your company’s business abroad. Mapping also allows scheduler’s to see exactly where crews and salesmen are at any given time, allowing them to easily add in additional appointments. Read More...
Kerio Connect: New Webmail & Tutorial Videos
It is completely cross platform and works on Macs, PCs and mobile devices. This means everything is integrated even if Windows users are using Outlook and Mac users are using Apple Mail, Address Book or iCal. Kerio Connect can be run on your own internal server or hosted by CranstonIT in the cloud. Read More...