Why you should always keep Find My iPhone enabled
Let’s start by being Captain Obvious. If you take your iPhone® everywhere, there’s always that chance you could leave it anywhere. Already have, you say?
Find My iPhone is an app that helps you find not only your iPhone, but your misplaced iPad®, iPod touch®, Apple Watch®, AirPods® or even your Mac®. The feature does what it says. If you lose your iPhone, you can identify its last known location by checking the Find My iPhone app or accessing the iCloud® website. The app will play a sound on your device to pinpoint the location, while iCloud will let you view your iPhone’s location on a map. Mystery solved.
Protect your network — and your data — with Kerio Control Firewall
Further, PCI compliance regulations now place the responsibility for data breaches on the business where the breach occurred. Along with this added liability, HIPAA and other privacy regulations are more strictly enforced than ever before.
CranstonIT understands the growing concern around data security, and offers next-generation firewall capabilities that protect against cyber attackers. One such powerful solution comes from Kerio Control, deploying unified threat management without complexity. Read More...
Make CrashPlan Your Backup Plan
You don’t have to be caught unaware if your computer crashes. Read More...
Endpoint Protector 4 Protects Your Company’s Greatest Assets
Endpoint Protector 4, a full Data Loss Prevention (DLP) and Mobile Device Management (MDM) product available for Windows, Mac OS X, Linux, iOS, and Android mobile devices, can help eliminate the risk by protecting your network and sensitive data from these types of threats. It will also help your company maintain compliance with HIPAA and other privacy regulations. The product provides protection in several different ways depending on the system or device. Read More...
Protect Yourself from Nebbiness on Public Networks with Cloak
In Pittsburgh we have a term we use to describe nosey neighbors, friends, in-laws, and even pets. They’re all “nebby” if they can’t keep their nose out of our business. Most of the time, nebbiness is relatively innocent, but when hackers get nebby, we need to do whatever it takes to protect our privacy.
Did you know that every time you use a public network – in a coffee shop, hotel, airport – you’re making your activities and personal information available to everyone else on that network? While most people don’t have the knowledge or interest in accessing this information, hackers do.
Protect Your Network with Kerio Control Firewall
Kerio Control offers a complete firewall solution that provides multiple types of protection called Unified Threat Management. This all-in-one solution will protect your network from malware, viruses, and malicious activity through a vigilant system designed to keep the bad guys out. Read More...
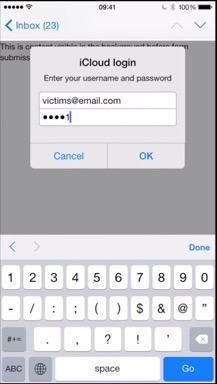
iOS Security Issue Attempts to Steal Username/Password Information
To remove the threat, return to Apple Mail and click Cancel on the login window if it reappears, then delete the email message that you were viewing when the login window appeared. As long as you don't enter your username and password into the window, you are safe.
If you have any questions about this security issue, give us a call at (888) 813-5558. Read More...
Coin: The Electronic Credit Card
Knock to Unlock - Knock iOS App
With Knock unlocking your computer is as simple as physically knocking on the face of your iPhone. The computer will automatically pick up the iPhone signal when you are within range of your computer allowing it to unlock. When you and your phone walk away from your computer, the minute you get out of range, your computer locks itself, making sure you never forget again. What if you forget your phone? No problem, just type in your password the old fashioned way and if your phone gets lost or stolen all you have to do is disable the application on the computer. Knock uses bluetooth to connect with your computer without draining your battery. Read More...
The new iPhone 5C and iPhone 5S
The most striking thing about the iPhone 5c is it’s stunningly bold colors. The first iPhone to ever be available in any color other than black or white, the 5c has five color choices: green, blue, yellow, pink, and white. Apple specially designed six colorful cases that add even more fun to the 5c. The cases feature circular cut outs that allow the color of your iPhone shine through while adding their own pop of color. The 5c is made of a single plastic outer shell, reinforced with steel framework making it much stronger than other plastic phones. Mix and match colors to make your iPhone uniquely you. iPhone 5c comes equipped with the A6 processing chip, making the phone fast while improving battery life. The new 8MP iSight camera takes even more stunning photos, and the HD FaceTime camera makes face-to-face conversations even better. Apple has managed to give you all these features with an even cheaper price tag. The 5c starts at just $99 for a 16GB phone or $199 for 32GB with cellular carrier contract. Read More...