Apple Pay: The easiest way to pay … everywhere
It’s only natural to feel reticent, even suspicious, when considering a technology such as Apple Pay®.
In theory, it feels nuts to cozy up to a payment terminal with your phone or watch to make your money disappear.
But Apple Pay and similar technologies that leverage information encryption are here to stay. That’s because Apple Pay is easy to use, preserves your privacy and enhances your financial security. It’s more secure than using a credit card — by far.
Apple Pay works with your iPhone®, iPad® and Apple Watch® and allows you to make secure purchases in stores, with apps and on the web. There’s no app to download, it’s easier than using a credit or debit card and faster than opening your wallet to do so. Simply hold your device within an inch of a compatible payment terminal — and they are virtually everywhere — put your finger on the Home button to use Touch ID® (or double-press the iPhone X’s side button and authenticate via Face ID® or double-press the Apple Watch’s side button), and you’re done. (Plus, Apple Pay Cash, launched with iOS 11.2, allows you to make and receive person-to-person payments in the Messages app or even by asking Siri. Wow.)
So how does this seemingly magical technology work?
Protect your network — and your data — with Kerio Control Firewall
Further, PCI compliance regulations now place the responsibility for data breaches on the business where the breach occurred. Along with this added liability, HIPAA and other privacy regulations are more strictly enforced than ever before.
CranstonIT understands the growing concern around data security, and offers next-generation firewall capabilities that protect against cyber attackers. One such powerful solution comes from Kerio Control, deploying unified threat management without complexity. Read More...
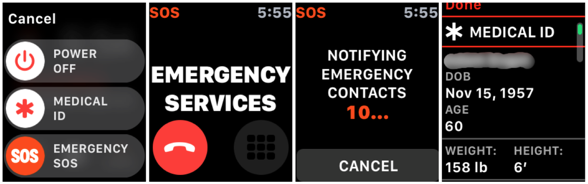
Emergency SOS on iPhone and Apple Watch offers 911 alternative
Apple® has added one more tool to the Swiss-army functionality of its iPhone® and Apple Watch® — and this one could save your life.
With Emergency SOS now available on iOS11 or watchOS®3, you can quickly and easily call for help and alert your emergency contacts. And there’s no additional app to buy or software to load, as Emergency SOS rides onboard and ready to activate when you need it most.
Emergency SOS accomplishes three critical tasks. First, it calls emergency services using whatever number is appropriate for your location, especially important when you are traveling abroad. Next, immediately after your emergency call ends, it sends a text message with your location to the emergency contacts you’ve previously established in Apple’s Health app on your phone or watch. Finally, Emergency SOS displays your medical ID so first responders can be alerted to medication allergies or other preexisting conditions.
Watch Out for Phishing Attacks Hidden in Your Email
Online criminals know we are all busy, and that we often aren’t focused on what we are opening, reading and where we are clicking. They take advantage of that inattention by forging email messages to look like they've come from Apple, Facebook, and Amazon, along with well-known banks, payment services, retailers, and even government agencies such as the IRS and the Social Security Administration. Even more dangerous are messages that appear to come from a trusted individual and include personal details—often targeted at executives and company managers.
Generally speaking, these attacks are called phishing. And they cost businesses hundreds of millions of dollars every year.
The goal, of course, is to prompt you to click a link in the message and visit a malicious website. That site usually continues to masquerade as being run by a company or organization you trust. Its aim is to sucker you into revealing confidential information by asking you to log in, pay for a product or service, or fill out a survey. The site — or an attachment in the email message — might also try to install malware. Although macOS is quite secure, it can still be affected if you approve certain security prompts.
Here’s how you can help identify potential phishing attacks. Read More...
iOS: Next Level Security with Face ID on iPhone X

It’s natural for one to be suspect about a new technology that is so complex, so advanced and so … different. For many, that’s the case with Face ID, now found on on the iPhone X.
The home button, a fixture since the original iPhone, is gone. To replace that Touch ID sensor, Apple has developed a new facial recognition technology that scans your face to authenticate you as the user. Apple claims that Face ID has a false positive rate of one in a million, except in highly unusual situations like identical twins or high quality 3D printed masks of your face.
The point is that while Face ID is more secure then its Touch ID predecessor — and its fingerprint recognition — it is not infallible.
Let’s understand how Face ID works. Read More...
Protect Your Data When Traveling
There is nothing more unsettling than being separated from your computer, if only for a few moments. And with the advent of the summer travel season, especially if flights are involved, it’s almost inevitable that separation will happen.
The U.S. Department of Homeland Security and the TSA have recently announced new regulations that ban technology larger than smartphones on certain flights heading in and out of the country. In fact, the Trump administration ordered nine airlines to prevent passengers from bringing computers and tablets into the cabin for U.S. bound flights. Instead, those devices must now be carried in the hold.
In addition, many airlines now specifically state they will not be held liable if these devices are lost, broken ... or breached.
If you encounter a situation where your personal computer is required to be stored in a checked bag, there are several steps you can take to protect your device and your data.
Beware of Sophisticated Email Scams
Here is how the scam worked:
The scammers first did some research on the company and found the names of the President and Controller, most likely using the company’s website or LinkedIn profile. Though email addresses for these individuals were not listed on the website, most companies use a standard naming convention for email addresses and guessing a user’s email address is not difficult. Read More...
1Password Is the Solution for Password Protection
Every. Single. Site.
You’re doing that, right?
Most of us use our pet’s name with a birthdate stuck on the end or something similar. And we use the same password for multiple sites because 1) it’s too difficult to remember a different password for every site, 2) we don’t keep a record of every password we create, and 3) we’re just plain old lazy. Read More...
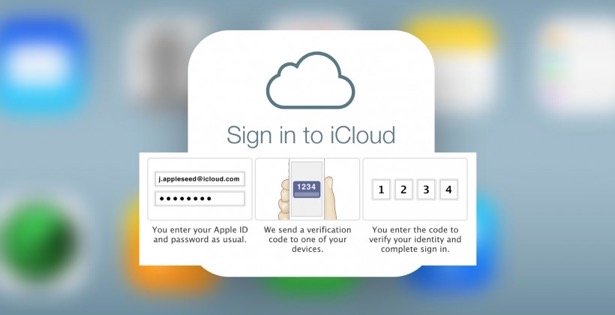
Two-Factor Authentication Adds Extra Protection For Your Apple Account
Protecting your identity and account information from theft and misuse is becoming more and more challenging. For Apple and Mac users, where all activity revolves around an individual Apple ID, protecting the information stored in your account is especially critical. Apple has added an extra layer of security to the log in process on new devices—in addition to the standard password protection--to do just that.
Two-factor authentication is designed to ensure that your account can only be accessed on devices you trust, such as your iPhone, iPad, and Mac, and only by you. When you sign in to a new device for the first time, you need to provide not only your password (factor 1), but also a six-digit verification code that is automatically displayed on one of your trusted devices (factor 2). This extra layer of security ensures that only you can access your account, even if someone else knows your password. By entering the code, you’re confirming that you trust the new device. Think of it like an electronic version of a job reference. Your trusted device is providing a reference by indicating that the newcomer is ok.
Endpoint Protector 4 Protects Your Company’s Greatest Assets
Endpoint Protector 4, a full Data Loss Prevention (DLP) and Mobile Device Management (MDM) product available for Windows, Mac OS X, Linux, iOS, and Android mobile devices, can help eliminate the risk by protecting your network and sensitive data from these types of threats. It will also help your company maintain compliance with HIPAA and other privacy regulations. The product provides protection in several different ways depending on the system or device. Read More...
CranstonIT No Spam Gets to the Root of Your Spam Problem
 Spam has an unfortunate similarity to gray hairs. Pull one, and two more seem to pop up in its place. Besides being just plain old annoying, spam can also present a major threat to security via the viruses and malware that often accompany it. Managing it is a colossal time suck that no one enjoys. To stop it, you need to get to the root of the problem.
Spam has an unfortunate similarity to gray hairs. Pull one, and two more seem to pop up in its place. Besides being just plain old annoying, spam can also present a major threat to security via the viruses and malware that often accompany it. Managing it is a colossal time suck that no one enjoys. To stop it, you need to get to the root of the problem.If spam has you pulling your hair out, we’ve got an easy solution available to our clients. CranstonIT No Spam is an email security system that stops spam before it reaches your inbox or the inbox of your staff and family members. Because it’s cloud-based, there is no software to download, making it super simple to set up and manage. That’s right. It’s a hassle-free, no-need-to-waste-hours-figuring-it-out solution. And, it detects 99.7% of spam while also blocking nasty malware and viruses. Read More...
Pulling the Curtains on Your Electronic Window
Today is your lucky day! There are more people than you can possibly imagine who want to know everything about you and are willing to pay for this information. They’re just not willing to pay you. And you’ll never actually meet them, either.
Have you ever noticed that immediately after shopping online for area rugs, you start to see rug ads in the margins of the web pages you visit or in the ads that appear in your Facebook timeline? Spyware and trackers are used by many companies as a marketing tool. It’s a form of adware that tracks your internet browsing habits and uses this data to deliver in-page ads targeted specifically to you. Read More...
Be Ware of Ominous Pop Up Warnings in Your Browser
One popular way these internet scumbags attempt to lure us into their evil web is to plant an ominous warning that pops up on our monitor foretelling of grave danger ahead if we don’t act fast.
“Warning!” it says. “Your computer has a malicious virus.”
The message is almost always accompanied by a tech support phone number. Call this number and they are only too happy to bill your credit card a hefty sum. Read More...
Drowning in spam? Here’s how to send those spammers running.
Spam, or unsolicited emails sent to a large number of recipients, is an unfortunate byproduct of our online activity. Anytime you share your email address, you increase your chances of receiving spam. This includes posts made to online forums or web sites, online order forms that require an email address, web site registrations, job inquiries, blog subscriptions, and even emails sent to friends. Some companies share your information with partner vendors, while others sell it to the highest bidder. Even if you only share your address with a select few, if your friend’s account is hacked, the spammers gain access to their address book.
It’s easy enough to stop legitimate spam received from companies you know. Simply click the unsubscribe link at the bottom of the email to be removed from the mailing list. This will either unsubscribe you immediately or take you to a preferences page where you can unsubscribe altogether or limit the number and frequency of emails you receive. Marking this type of message as “Junk” often doesn't work well because businesses try very hard to craft messages that ensure their emails do not end up in a Junk folder. Read More...
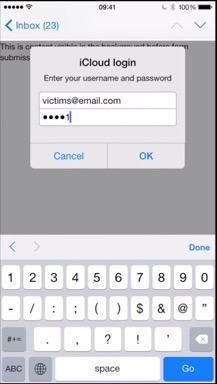
iOS Security Issue Attempts to Steal Username/Password Information
To remove the threat, return to Apple Mail and click Cancel on the login window if it reappears, then delete the email message that you were viewing when the login window appeared. As long as you don't enter your username and password into the window, you are safe.
If you have any questions about this security issue, give us a call at (888) 813-5558. Read More...
Clean Malware Off Your Computer with Adware Medic
Apple Pay - Revolutionizing the Way We Pay
Apple Pay works both in physical retail stores and online. The Near Field Communication antenna that is built into the iPhone 6 enables you to pay simply by placing your finger on the fingerprint scanner and being near a contactless reader. Your iPhone will then vibrate or beep, letting you know your payment was successful. Apple Pay will also be available on the Apple Watch when it is released in April. You can also use Apple Pay on your iPhone 6, iPad Air 2, and iPad Mini 3 at select online retailers, such as Airbnb and Target. Read More...
SSL Poodle Bug
Protecting Against Malware on OS X
Stolen MacBook Returned Using Find My iPhone
Common Internet Scams
Phishing is an email scam that uses well known companies to trick you into giving sensitive information. Here’s how it works: you get an email for a company, such as your bank, saying they need you to immediately sign into your account and provide a link for you to do so. Once you click on the link, you are taken to a website that looks like that of the trusted site. If you provide your login credentials, they are saved and used to access your account. If you receive an email requesting sensitive information, it is probably a phishing scam. Read More...
Introducing Watchman Monitoring for Contract Customers
Watchman Monitoring is a new program available to all our residential and business customers using Macs. The program operates under a simple idea: catch a problem quickly when it occurs, and that’s exactly what Watchman Monitoring does. We install the Watchman program on your computer and it runs hourly checks to ensure that everything is running smoothly. Read More...
1Password - Effective Password Management
Stop Computer Theft
How do you protect yourself? The most important actions must be taken before your laptop is ever stolen.
First, think about your data. For many of you, your data is more valuable than the computer itself. So, you must frequently backup to an external hard drive or a cloud based service like ClouDox. This helps ensure that your data is backed up and can be restored if needed. Read More...
Managing Your Mail
Keeping your Mac Safe with Mountain Lion's Gatekeeper
Keep Track of your iPhone, iPad and iPod with Find My iPhone
The Find My iPhone service is built right into your iPhone 4, iPad or fourth generation iPod Touch. All you need to do is activate it. Then you can track a lost device from any computer. Read More...
Understanding Malware and Mac Security
One malware scam is specifically targeting Mac users. Hiding behind names like Mac Defender, Mac Protector or Mac Security, this phishing scam convinces people to download harmful software. Read More...